
Most of us have heard of WiFi beaconing or beacon flooding, or not? So what is it exactly and why does it matter for the purpose of this article? Before we dive into it, let’s explain some basic concepts we are going to be using.
We usually consider wireless access point (AP) or multiple APs in the same extended service set (ESS) as one unified network. If we break it down further we will see that each ESS consists of multiple basic service sets (BSS). So, in reality, each AP has its own set of services, and each service is on its own VLAN.
In order for a WiFi AP network to be visible to clients, each SSID on each band broadcasts a unique beacon frame. The beacon frame is a periodic advertisement broadcast from the AP to tell any listening devices that this SSID is available and has particular capabilities.
Think of it as one of those spinning sign advert guys that shout at people who pass by.

Client devices depend upon these beacon frames to discover what networks are available (passive scanning) and to ensure that the networks that they are associated with are actually still present and available.
Each beacon frame (or probe response) contains a bunch of information about the specific SSID being offered. To mention some: SSID, BSSID, channel frequency, country, beacon interval (how often AP sends beacons out), etc.
A client also has the option to perform probe requests (active scanning). In this case, a client device sends a request to the AP to see what networks are available, and each SSID from each AP in range will send out a unicast (probe response) that has the same information as a beacon frame.
Important difference
It’s important to note here that while WiFi beaconing is just an AP setting up multiple SSIDs purposely to make each of these different SSIDs an “independent” network, probe requests are considered as active scanning and can be taken as Distributed Denial-of-service attack (DDoS). That’s because probe flooding can overwhelm the AP and even take it down temporarily. As this is illegal in many countries, it is important to distinguish it from beacon flooding we are discussing here.
What this means is that we can broadcast hundreds or even thousands of fake access points. Others that are in the area will see all of these fake access points and their names when they search for WiFi to connect to. As you can probably see, SSID flooding is not a denial of service. However, this is still a pretty cool trick.
Now that we got this out of the way, let’s go back to the subject.
Beacon frames are usually utilized in:
- Stress testing the WiFi network
- Deauthentication attacks
- Probe request/response sniffing
- Hiding your legitimate wireless AP in a sea of fake access points (a sort of security through obscurity)
And last but not least, it can be used to exfiltrate or leak data, play games, and troll your friends but also save lives.
How I got the idea for this WiFi beaconing use case you might ask?
Well, being stuck in an elevator for 2.5 hours, in an unfamiliar building, without anyone hearing me banging the doors. I had no access to the internet and no GSM to call for help. It got me thinking about these alternative ways of sending a message out. Making a bunch of new SSIDs like “THERE IS A PERSON STUCK IN THE ELEVATOR! SEND HELP!!”, would probably do the trick! I’m hoping to remember this next time, if I ever get stuck in an elevator for a long time, or I get caught under some ruin due to an earthquake. Things can be unpredictable sometimes and one can never be careful enough.
SOS Wifi Beacons
You can do this in any Linux distro, also Termux on your phone, a Raspberry Pi, or a simple ES8622 chip.
Install these two tools:
apt-get install airmon mdk3Wireless chips have 3 modes: client mode (regular WiFi client), interface mode (acting as AP), or monitor mode (monitoring traffic).
Put your device in monitor mode:
airmon-ng start INTERFACEINTERFACE is your WiFi adapter usually wlan0 or wlan1 if you have an external dongle or second WiFi card.
Create a text file with the name ssid_names.txt (or whatever you like) with a list of SSID names you want to see, each separated by a new line.
nano ssid_names.txtType your message in form of SSIDs, or even encrypt it if it’s not meant for everyone to see in the plain text! In this case, I chose to raise some neighboring eyebrows with some classic Rickroll trick.
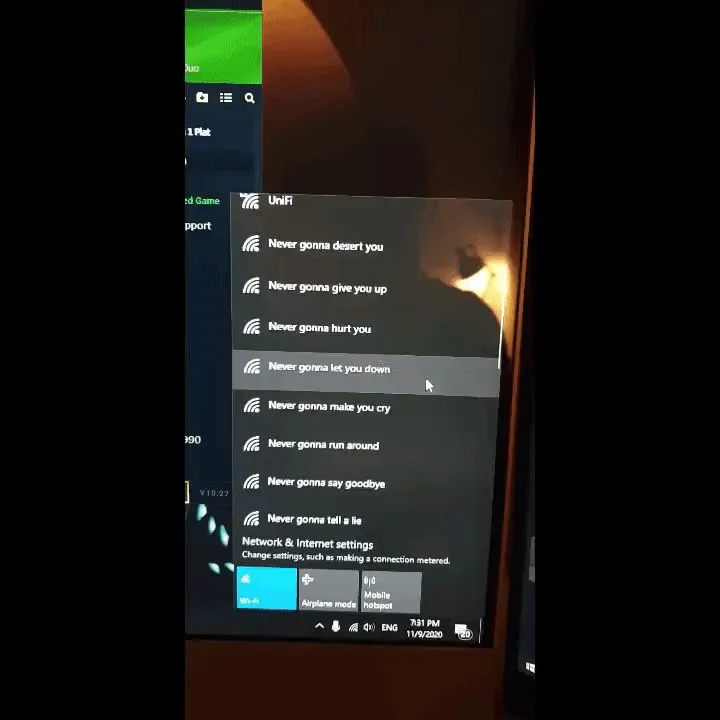
If you prepare your list ahead of time you can pull this off in 2 commands.
To begin transmitting the beacon frames, we’ll use the mdk3 tool with the b (beacon flooding mode), -a (advertise a WPA2 network), -g (advertise a 54Mbps network) and -f (use the provided dictionary file):
mdk3 MONITOR_INTERFACE b -a -g -f ssid_names.txtMONITOR_INTERFACE is your WiFi adapter with suffix mon for monitor mode, eg:
mdk3 wlan0mon b -a -g -f ssid_names.txtIt’s worth noting that you can’t target specific wireless devices, but you have the ability to specify the channel number.
mdk3 wlan0mon b -a -g -f ssid_names.txt -c CHANNELThe challenge is can you think of some more cool use cases for WiFi beaconing?
Thank you for your time and go do stuff now!

